HACK Issue 16: The Threats and Security Matrix, Cloudflare shows us bug bounty do's and dont's, and Shoot your shot

As I write this, the Kentucky Derby is on TV and the announcer just said they have 150,000 people in attendance, first time since the pandemic that it's been a capacity crowd. So great to see! And tis the season, I just announced yesterday I'll be in Denver May 18th hosting a hacker meetup, and I'm busy planning multiple events, one of which I teased on Twitter (watch Wednesday for an announcement). Humans are social creatures, and we are being social. <3
Cloudflare bug bounty program: a case study in what to do and not to do
The Assetnote team launched a 3-part blog series on some impressive research into Cloudflare. The tl;dr at the end of it:
So, if you’re still with us at this point in the epic, as a final takeaway for defenders... In complex network environments, ensure appropriate network segregation and firewalling is in place that reflects the various security boundaries of your application.
A few things stood out to me in this: No. 1 is the way in which Cloudflare handled the interaction (and how Assetnote went out of their way to thank them and even HackerOne for working with them 👏).
And this, ladies and gentleman, is how you collaborate with researchers. Quick fixes, give credit, coordinate and share. pic.twitter.com/cFXOdrFfKa
— Luke Tucker (@luketucker) May 7, 2022
The 2nd thing that stood out to me, however, is the basement level bounties that Cloudflare advertises in their public bug bounty program. To me, this clearly shows a disconnect internally at Cloudflare. Typically if you are great at being responsive and giving hacker's recognition, then you offer competitive rewards. But there's either a lack of belief in the model, or a lack of political will to fight for the necessary budget to run a world class public bug bounty program and attract top talent. 🤷♂️
They would have a LOT more attention on their attack surface from the bug bounty community if they 10x their bounty rewards - they've got the process, recognition, and transparent pieces already so the other 3 key steps would be to increase rewards and increase education or expand product or testing access to hackers for advanced testing.
They should really count their lucky stars that Shubs, Sean, and the Assetnote team went as deep as they did. It sure wasn't for the bounties, likely it was for strategic business reasons given the Assetnote product and the importance of security research to their brand awareness and brand credibility.
How well can a company stop the largest cyber attacks?
Every cybersecurity vendor would like a score, a measurement of how good they're product helps improve the security of a company to increase sales. Everyone is leery of the "here's your score, you're welcome" kind of attitude from vendors, however. The best I've seen is companies giving a "configuration" score which basically is a measurement of how effectively a company is using the tool. The vendor should be the expert in its tool setup, and as long as you have a good measure on integrity of a vendor, that is useful.
I found this post shared in a security slack channel I'm apart of, and thought it was interesting:
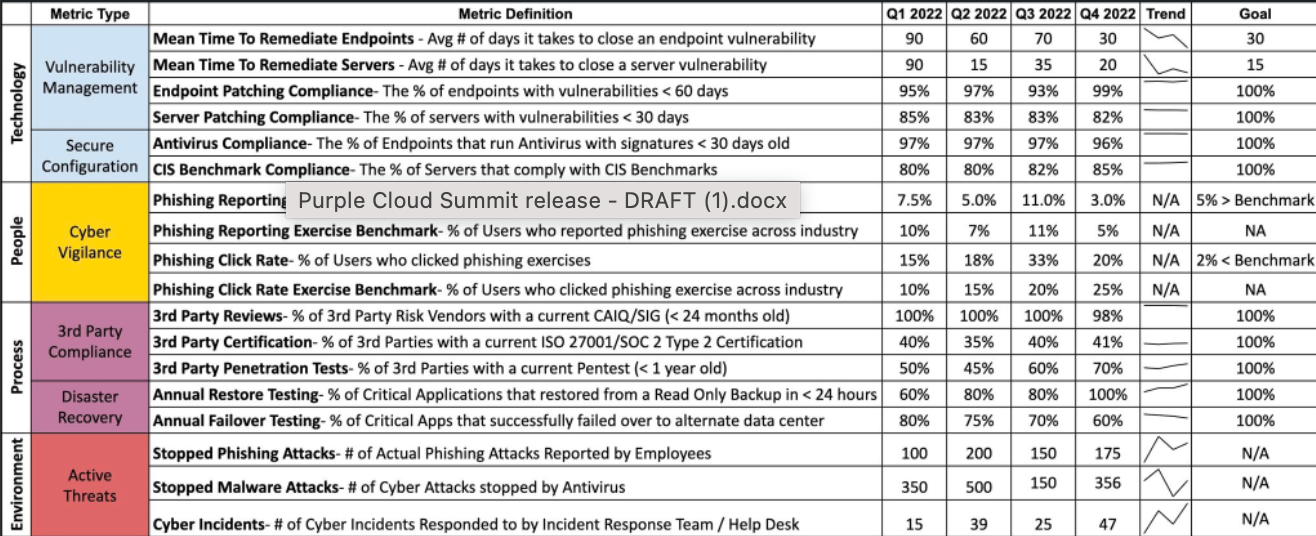
Read more about the Threats and Security Matrix on OWASP's site.
Inspirational note
"The two were running together; and the other disciple ran ahead faster than Peter and came to the tomb first." - John 20:4
Every time I read this verse or think about it, I laugh to myself. John is the "other disciple" referenced so here's the apostle John talking about this epic moment in history and he decided to memorialize forever in Scripture that he ran faster than his friend Peter. Just a reminder not to take ourselves to seriously and to shoot your shot. 😂
