AWS Security Bulletins and Cloud Security Researcher Trends
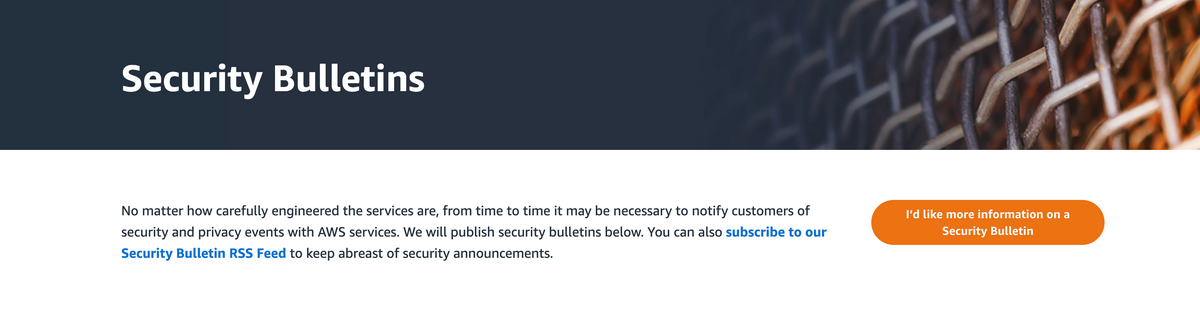
In the last 5-years, AWS has published on average just over 7 security bulletins per year.
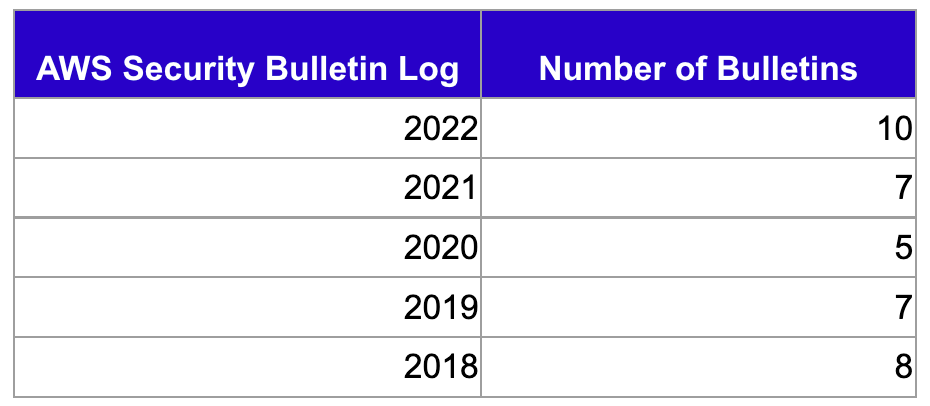
This year has seen the most bulletins published since 2017 when there were 12 (though 8 of them were related to the Xen hypervisor so you could argue there was more like 4 - 5).
If one were to just look at the number of security bulletins published, there isn't a trend per se. But let's add another column.
I went back through 10-years of security bulletins, and found two bulletins before 2022 that referenced security researchers and thanked them: Reported SSL Certificate Validation Errors in API Tools and SDKs and Resolved: Application Load Balancer Session Ticket Issue .

Most of the bulletins would reference a CVE or note that they were "aware of recently disclosed security issues" but nothing else.
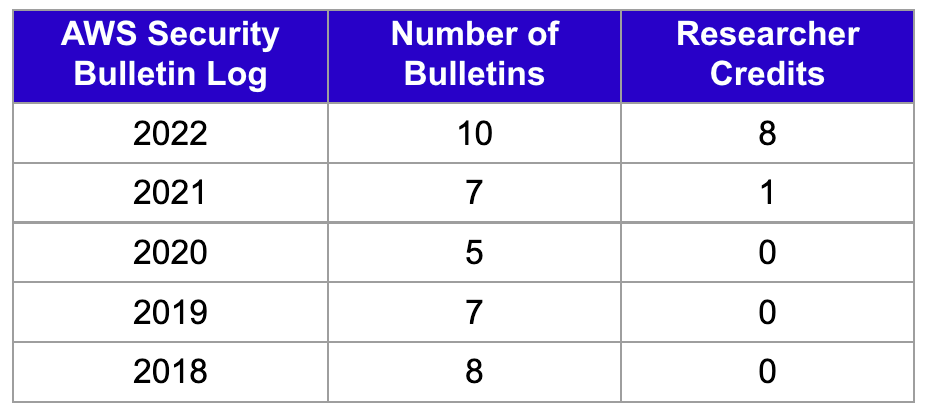
Here's the full list of 2022 bulletins and researcher / vendor credits:
I see two trends (both good):
Increased security researcher focus and talent on cloud service providers. Back in 2012 it was mostly academics doing deep dive research so there was less attention and opportunity for AWS to note credit. Today, in cloud there are dozens of vendors employing cloud security researchers. More focus, more time for existing talent to increase in proficiency and new talent to join the ranks. Plus the attack surface continues to grow (509 AWS services and counting).
AWS recognizing the contributions of the researcher community and learning from past mistakes. In December 2021, Lightspin's VP Security Research Gafnit Amiga found a vulnerability in AWS Sagemaker. There was no security bulletin published. In April, Gafnit published AWS RDS Vulnerability Leads to AWS Internal Service Credentials. At first, there was no security bulletin published for it and then they rushed one out that originally didn't include Lightspin or Gafnit as credited. The community noticed:
I'm glad someone has noticed this. We asked AWS weeks ago if there would be a security bulletin (we were told no). We asked for a quote for the blog (like they provided other vendors earlier this year) and were also told no. Not sure why the inconsistency 🤷♂️. https://t.co/18asVQf6AR
— Luke Tucker (@luketucker) April 12, 2022
Others in the community kept asking the hard questions like "why are we finding out about AWS security issues from vendors, not AWS official channels?" I think the data in 2022 shows AWS' efforts to a) give credit to researchers and b) leverage official channels like security bulletins for customer security awareness is trending in a good direction.
Conclusion
I applaud the AWS security outreach team for driving change. I'm sure it's not easy. And while things aren't perfect, I'm encouraged by what I see. I definitely think there's more opportunities to continue to improve the expectations on both sides. For instance it's still not clear to me when and why a security bulletin is published vs not?
And I know disclosure is a sticky issue on both sides, I get it. Companies can throw their weight around and force security researchers to follow their disclosure terms "or else". I'm not making any deep commentary on that in this post, I know it's a briar patch but not one I'm going to navigate through today haha. At least in most cases I've seen, AWS is supporting coordinated disclosure and allowing deep technical posts to get published by the research community. More than I can say about many other companies.
And I also know from my years at HackerOne: researchers don't have a full understanding of what the security team members they're working with have to deal with internally: from internal product and engineering teams to PR teams to Legal... it can be a LOT especially at a company as big as AWS. It can be frustrating for a researcher to feel like the security team is "dragging their feet" or "yanking them around" but often they're in the middle trying to appease both internal stakeholders and the external researcher.
I look forward seeing more empathy on both sides of the equation, more formal opportunities to give researchers a stage to "show and tell" about their finds for their individual career benefit and the collective benefit of the broader security community.
